Cloud native workloads terminology is used a lot these days to describe new technologies and deployment models of applications in the cloud universe. Serverless is a notable example of such cloud native-workloads: it prioritizes simplicity and agility over compatibility, control, and performance SLAs. It’s a revolutionary concept that abstracts away infrastructure concerns and provides a simple execution environment. Serverless comes with significant cost-savings, charging only for “execution” time in sub-millisecond billing units, and not charging for idle time. Scaling and high-availability are additional benefits that applications gain when deployed in a managed serverless cloud environment.
The Evolving Landscape
Although AWS launched the first Function-as-a-Service (FaaS) offering, AWS Lambda, as far back as 2014, today Serverless is a concept with a broad spectrum of services. All serverless modalities share the operational abstraction, cost savings model and infinite scaling options. Functions (e.g., AWS Lambda, Azure Functions and Google Cloud Functions), Containers-as-a-Service (Fargate, ACI) and even database queries (Aurora) all are offered in this new serverless model.
We at Aqua identified the inherent security challenges of serverless architectures some time ago. Our serverless containers security solution is now widely deployed by multiple customers. As we’re witnessing growing demand for securing serverless functions, we’re adding additional security features for serverless functions.
Threats to Serverless Functions and Aqua’s Approach
Investigating the attack surface and the threats of serverless functions reveal 2 distinct attack vectors:
- Application code vector: Includes potential attacks that can be carried out by external users, leveraging a weakness or a vulnerability in the Serverless function code, outsourced libraries, OS dependencies etc.
- Serverless environment: Refers to weaknesses or vulnerabilities inside the cloud infrastructure where the serverless function is executed.
Our solution for securing serverless functions addresses these vectors and minimizes their potential impact:
- We minimize the application code attack surface of serverless functions by scanning the function’s code for open source components, external libraries and OS dependencies.
- We correlate the results with our vulnerabilities database to identifies potential vulnerabilities.
- We also scan the code alerting about secrets that are stored insecurely in the code. These scans are automated and continuous, discovering new functions and alerting on newly discovered vulnerabilities.
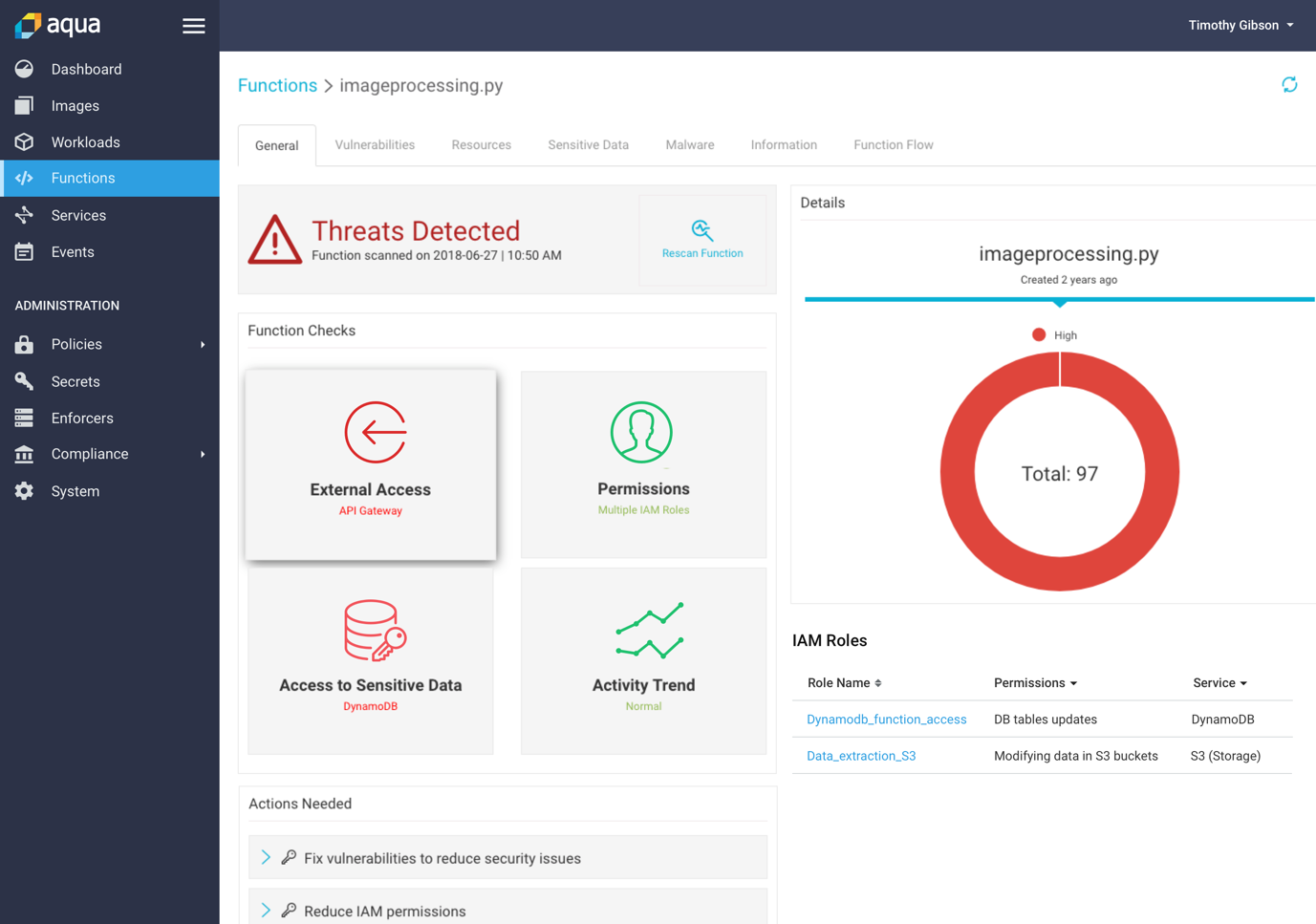
But we wanted to increase the security level and extend the scope beyond application code and hard-coded secrets, by also addressing the security layer of the serverless environment. One of the fundamental challenges in serverless functions is their permissions definitions (a.k.a. IAM roles, in AWS terminology). The function’s permissions are defined in a separate process, typically at the early development stage of the function’s code, and for every function independently. This granularity leaves room for potential mistakes or misconfigurations, which can lead to a potential attacker gaining access to a broader environment or to more services than the function requires. In addition, we identified scenarios where development teams tend to add permissions for services that might be used, but that eventually are not in use. Having such permissions endangers the security posture of your environment, leaving too many privileges open and making it hard to detect or track malicious activity. Many security researches already wrote on the need for a “least privileges model” and about the risk of using cloud vendors’ default permissions.
In order to address this risk potential, Aqua also scans each function’s permissions, identifying situations in which the function’s permissions exceed its needs, or aren’t actually being used by the function.
The result, as can be seen in the screen below, is an assessment of the function’s code threats (code vulnerabilities) and its permissions, providing recommendations for least-privleges implementation and the code substitution needed to mitigate the risk.
The important consideration we kept in mind was to avoid modification of the function’s code. Our scanning tool significantly improves the security posture of serverless functions without any code integration, modifications or changes. It complements the security solution we released at the beginning of 2018 for securing serverless containers, providing comprehensive security coverage for cloud native workloads and environments.
The use of serverless workloads is growing fast, with many organizations hitting the ground running while figuring out how to use them securely. We have no doubt that usage will continue to evolve and expand, and that the future is one of hybrid application architectures that will optimize across the spectrum of cloud native technologies for performance, cost and other tradeoffs. Aqua will be there to secure such applications, VM-based, serverless, and everything in between.

