GKE Autopilot is a new mode of operation in Google Kubernetes Engine (GKE) launched earlier this year to help DevOps teams focus their time and resources on building applications on Kubernetes, rather than on managing the infrastructure that the applications run on. As Aqua Security is a GKE selected security partner, customers can now run the Aqua platform seamlessly on a GKE Autopilot cluster. This can allow them to address the security risks and compliance requirements that can stand in the way of broader Kubernetes adoption and greater automation.
GKE Autopilot provides a fully managed Kubernetes service to reduce the operational overhead and lock down the infrastructure. In turn, as a GKE Autopilot security partner, Aqua helps DevOps and security teams tackle the need to consistently protect the applications and code they run on GKE Autopilot pods.
Along with out-of-the-box GKE Autopilot allow-listing for runtime security, Aqua also provides image scanning and assurance, dynamic malware detection and role-based access controls (RBAC) to help customers seamlessly integrate security and protection into the life cycle of their Kubernetes applications.
What is GKE Autopilot?
GKE was the first cloud-based managed Kubernetes service on the market and celebrated its sixth anniversary this year. Kubernetes itself was the brainchild of Google engineers and was released as an open source instantiation of the internal Borg project in 2014. Precisely because it was created by Google engineers for in-house container orchestration, GKE is considered one of the most advanced Kubernetes platforms available.
GKE Autopilot represents the next step in the adoption of Kubernetes, managing the entire cluster’s control plane, node pools, and nodes. By assuming management and maintenance of Kubernetes clusters, GKE Autopilot alleviates one of the critical bottlenecks that stand in the way of broader use of Kubernetes to automate orchestration and scaling of multi-cluster deployments.
GKE Autopilot and the shared responsibility model
As a direct (and intended) outcome of assuming responsibility for the management of GKE clusters’ control plane, node pools and nodes, GKE Autopilot enhances their security posture by locking down many of the native Kubernetes configurations that can leave implementations vulnerable to attacks or opportunistic exploits.
For instance, GKE Autopilot exposes the Kubernetes API to developers but, by default, removes permissions to use Kubernetes primitives like privileged pods, limits access to the Kubernetes host, and blocks access via SSH to nodes. This addresses many of the attack vector paths and techniques identified in the MITRE ATT&CK Framework.
In addition, the service assumes responsibility for maintaining GKE host hardening guidelines and enforces node shielding – using strong cryptographic identities to reduce the risk of attacks that take advantage of privilege escalation techniques and exploits that leverage exfiltrated pod credentials.
While GKE Autopilot can help to ensure security best practices and reduce the blast radius of attacks, customers are still responsible for securing the applications that run on the service.
Ensuring that security is integrated into DevOps processes, protecting workloads at runtime, and detecting and mitigating software supply chain attacks (like the recent compromise of a popular npm library) remain the customer’s responsibility.
How Aqua helps secure applications on GKE Autopilot
Our support for securing and ensuring compliance for workloads on GKE Autopilot builds on our integration with Google Cloud, availability on Google Cloud Marketplace and comprehensive Kubernetes security capabilities. It also aligns with Aqua’s broader strategy to enable secure adoption and automate protection at scale for multi-cloud architectures.
Aqua enables GKE Autopilot customers to collaboratively secure the applications that are built and deployed on the service — specifically the Kubernetes pods, which can run multiple containers with a shared set of storage and networking resources, and runtime logic.
Even as GKE Autopilot assumes broader responsibility for the underlying infrastructure than other managed services to date, container-based applications can still be vulnerable to outside attacks and exploits, such as:
- Supply chain attacks: Hiding malware in file encoding or compression
- Cryptomining attacks: Download of malicious code, or malicious networks communication
- Fileless malware execution attacks
Aqua’s set of capabilities for securing the full lifecycle of applications on GKE Autopilot includes:
- Image scanning for “shift left”
- Malware and supply chain attack detection
- Runtime security and networking policies for cryptomining
- RBAC and least-privilege access policies
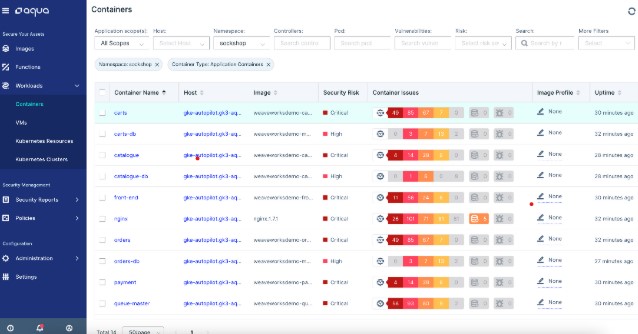
Image scanning for “shift left”
Since customers are responsible for the code that runs on GKE Autopilot, security best practices (as well as compliance mandates) require that DevOps teams have a process and tools in place to detect and identify known vulnerabilities in container images. Aqua’s market-leading scanner helps to “shift security left,” scanning artifacts directly in the CI/CD pipeline, Google Function Store, and image registries (such as Google Container Registry) to provide complete risk analysis and to facilitate rapid remediation during the build. The Aqua scanner can also identify and analyze OS packages and more than 40 programming language packages.
Malware and supply chain attack detection
Aqua supplements static scanning for known vulnerabilities and image assurance with Dynamic Threat Analysis (DTA) for malware detection and mitigation against supply chain attacks. Security teams can test running images and detect anomalous activity before production in a secure, hosted container sandbox that functions as an acceptance gate. DTA uses Tracee, Aqua’s open source project based on eBPF, combined with indicators of compromise detection rules maintained by Aqua’s research team.
DTA helps to ensure that those advanced threats and fileless malware execution in container images are detected before they are pushed to production, helping to maximize flexibility by integrating and automating analysis with current workflows in the CI/CD pipeline.
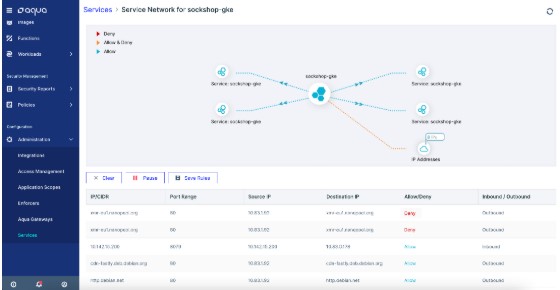
Runtime security and networking policies for cryptomining
Out of the box, any GKE Autopilot cluster that is created will be allow-listed for deploying the Aqua Enforcer component to provide runtime protection. The Enforcer allows customers to define and enforce a broad set of runtime policies, including drift prevention to maintain container immutability and prevent zero-day threats that exploit the software supply chain as an attack vector to launch fileless or other sophisticated malware.
The Aqua Enforcer policies also incorporate a cryptomining blocker that leverages a proprietary database maintained by the Aqua research team of malicious domains (IP and DNS) known to execute these attacks to deny network connections.
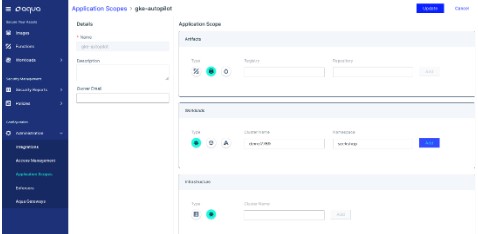
RBAC and least-privilege access policies
Aqua extends native Kubernetes role-based access controls with additional layers of policies to ensure least-privilege policies for multi-application access control. Aqua enables organizations to configure hierarchies and role-based permissions based on defined scopes, including distinct definitions of applications and environments. This helps to maintain separation of duties for security and compliance. Administrators can define custom scopes for each application based on specific pipeline attributes (for example, registry or image), workload attributes, and Kubernetes context.
Enhance security and compliance for GKE Autopilot clusters
GKE Autopilot’s managed Kubernetes service significantly reduces the operational load in maintaining the orchestration layer infrastructure and improves the security posture by locking down many native configurations that can get DevOps into trouble inadvertently. In turn, Aqua helps customers take responsibility for the security and compliance of their applications so that they can take advantage of the full scope of GKE Autopilot’s benefits.
Working together with the GKE Autopilot team, Aqua will deepen our support and extend our existing capabilities for integration of security best practices into the DevOps flow, including Dynamic Threat Analysis and runtime protection.
For more information, visit Aqua’s Google Cloud Marketplace listing and learn more about how Aqua helps customers secure and ensure compliance of their Google Cloud Platform deployments.