Attackers are sophisticated, there is always a lag between zero days and mitigation, and production workloads are critical. So why is the adoption of runtime security for cloud native applications still lower than shift-left security practices for the same applications?
We will discuss this, along with the solution, in this blog. Earlier this week, we introduced the next-generation of our runtime security solution. It is effective at stopping attacks, easy to deploy and manage, and nothing short of transformational for your security posture.
Runtime security matters
Let’s face it, your production workloads are both the most sensitive and critical part of the software development lifecycle, as well as generally what attackers are trying to access. And yet, in the cloud native application landscape, shift-left and vulnerability scanning at both the application and infrastructure layers are relatively well-adopted security capabilities, while adoption of runtime security controls at the application layer lags behind. (It’s important to note that security capabilities in runtime at the infrastructure layer are well-known and mature in the form of Cloud Security Posture Management (CSPM). It’s really runtime protection at the application layer where adoption falls behind).
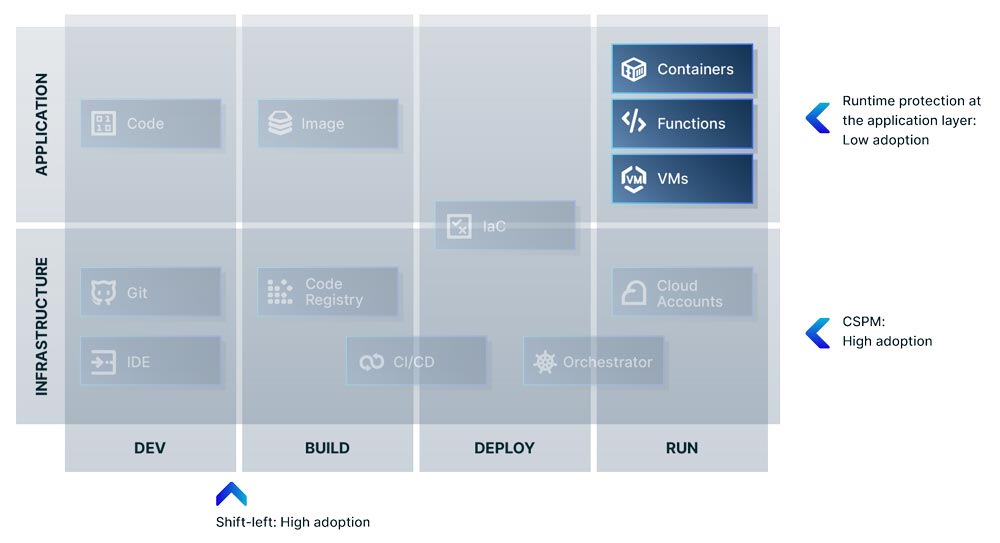
Why would this be? Well, for some teams, adoption of runtime security can be fraught with a perception of complexity and risk.
- First, security measures on running production workloads can be viewed as risky, especially by DevOps teams whose primary mission is speed. Today, many companies build on this perception to push the idea of ‘agentless’ security in runtime (see here for our blog on why agent vs agentless is a false choice); a concept that we will address in-depth.
- Second, for many teams, runtime protection requires knowledge of the application to know which policies to set. Security teams would have to work with engineering to understand the particularities of the application, which was a prohibitive practice in some organizations. And while many teams have been successful with this paradigm, some have been unable to overcome the internal obstacles to implementation.
We set about solving these challenges, and today, we are here to tell you that runtime protection is accessible for all teams. Runtime protection has never been optional to an effective security posture; and as a result, we are making it easier than ever.
The Right Kind of Visibility
Let’s start with the FUD. As mentioned above, some vendors will use the historical, perceived complexity of runtime security to push snapshot scanning technology, creating a false dichotomy between ‘agent and agentless’ protection. But in runtime, agentless technologies will only provide visibility into the runtime environment. Which is a good thing; Aqua offers snapshot scanning as a key part of our Cloud Native Application Protection Platform (CNAPP) because we think it’s a great way to achieve immediate visibility into risk.
Snapshot scanning identifies top risks in cloud runtime environments by combining cloud account misconfigurations at the infrastructure layer with sensitive data exposure, known vulnerabilities, and malware at the application layer.
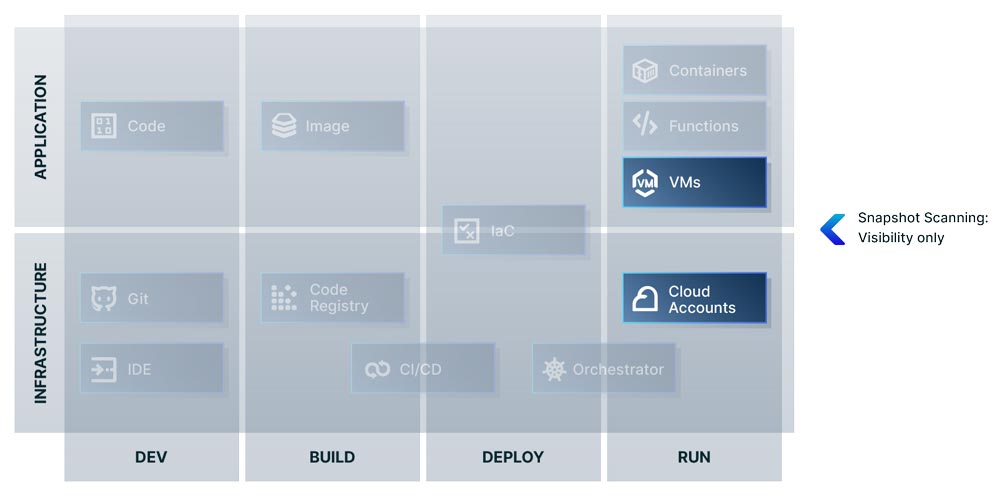
But snapshot scanning has never been an answer to the perceived complexity of runtime protection and it doesn’t provide the same kind of visibility. Snapshot scanning is time interval based and the data provided is based on whenever the cloud API did its last scan. These intervals can differ across vendors and there can be as much as a 15 minute gap between scans.
This matters the most to security operations teams that understand the impact of mean time to detect (MTTD) and mean time to respond (MTTR) metrics on their ability to adequately mitigate incidents. Mean time to detect, or MTTD, indicates the amount of time it takes your team to discover a potential security incident. Mean time to respond, or MTTR, indicates the amount of time it takes to control, remediate, and/or eradicate a threat after it has been discovered.
Dwell time defines the entire length of a security incident, the duration from which an attack first occurs in your network to the time it has been eradicated and your stack has returned to a balanced, healthy state.
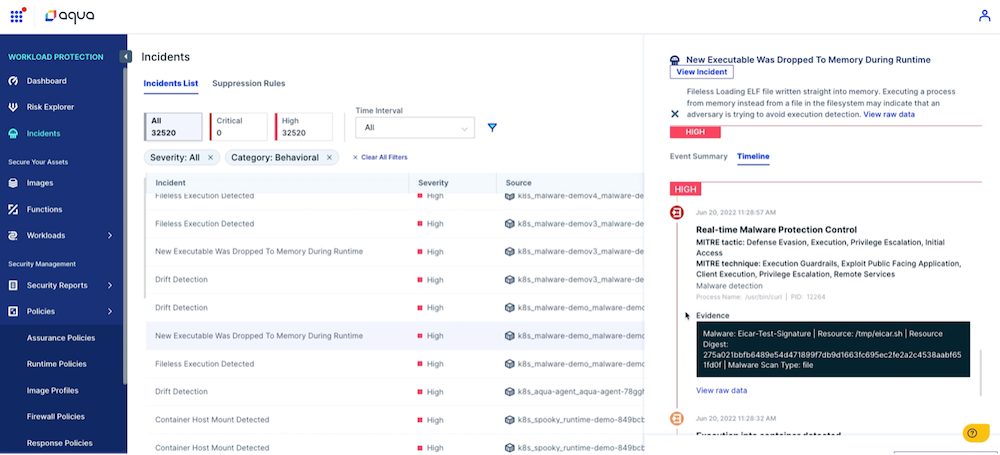
Fileless malware attacks and techniques like executing from /tmp will have too much space to play with snapshot scanning. If an attacker injects malware into /tmp, runs it, then deletes it before the next screenshot, they can clear their tracks seamlessly, without you realizing they were even there.
Low-level, and kernel level visibility matters
Ultimately, snapshot scanning does not give you visibility into the kernel level. It does not capture syscalls and attempts to execute from memory.
This results in lower data resolution. Without realizing it, you might have advanced malware like rootkits hiding themselves within the kernel.
Snapshot scanning also can’t give you the in-depth data needed to construct an attack timeline to quickly decide impact, mitigate it, and provide that data to governing and compliance bodies. Post-incident investigation is impossible for ephemeral workloads if you don’t have the syscalls of the container, and there are no leads to understand what happened. If something was downloaded from an IP or a storage service, you at least have data points to start connecting. Without that information, even if you detect a malicious event, you won’t know where it came from or who did it. You might save new files written to the disk to contain the malware file for investigation. But it would take an enormous amount of time and effort to formulate an adequate resolution and response.
Granular visibility and protection; why it is essential to make runtime accessible to every team
Moving to reality and the benefits of runtime protection, MTTD and MTTR for attacks such as log4j or Spring4Shell demonstrate why the realtime and response elements of runtime protection are critical. When the world became aware of those two vulnerabilities and a fix was made available, there was an unavoidable lag between the time to mitigate and the announcement of the issue. This means attackers had exactly as much time as that lag to exploit the vulnerabilities as you had to find and fix your exposure.
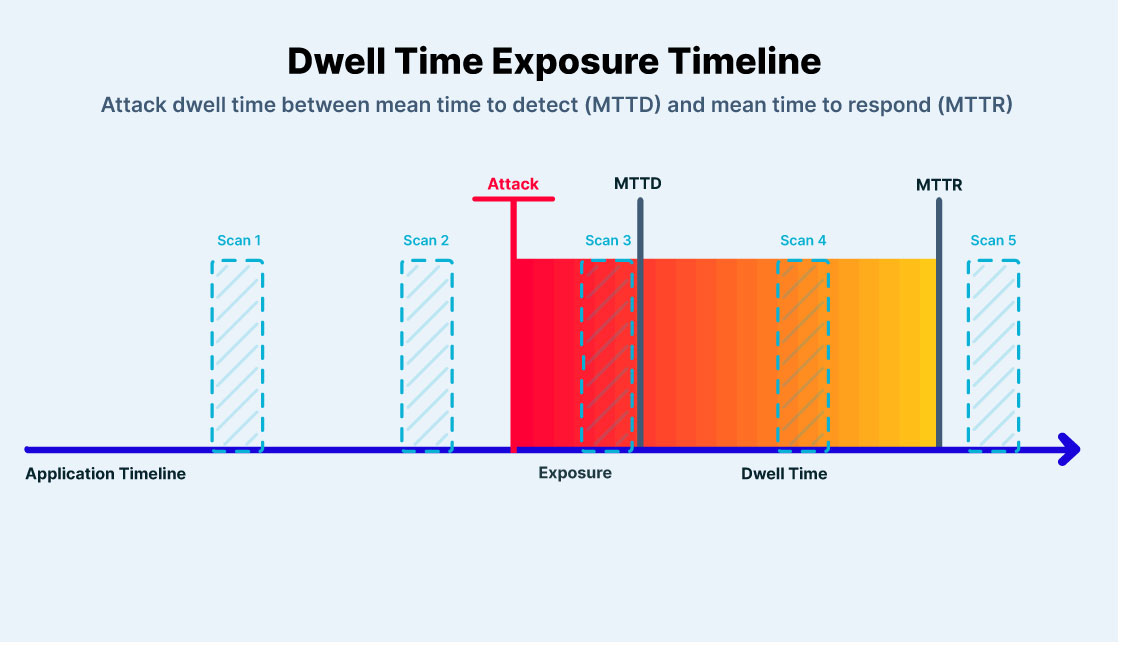
Runtime protection is what keeps that inevitable lag from becoming an incident. In the time that you are spending patching and preventing the issue, runtime protection will keep your exposed workloads from being exploited. Not to mention the fact that the right kind of runtime protection will stop unknown attacks and sophisticated attackers targeting your workloads.
The Next Generation of Runtime Protection
We get it. No more political battles implementing runtime. No more blind spots in your production workloads. You need immediate protection and deep, realtime visibility today.
Recently, we introduced Aqua’s new out-of-the-box, advanced runtime solution for seeing and stopping zero day threats. Protection is composed of a set of new, curated, and optimized default security controls that are based on years of experience deploying industry-leading granular runtime security. Using eBPF technology and threat intel from cyber research team Aqua Nautilus to identify advanced threats, Aqua surfaces the most critical issues in realtime while also implementing a set of controls to protect running workloads immediately, without disrupting the business.
As a result, you get protection in minutes without an in-depth knowledge of their applications and without unnecessary risk to production workloads.
Policies are applicable for containers, VMs, and Kubernetes workloads. For example, here are the curated container policies.
Container policies
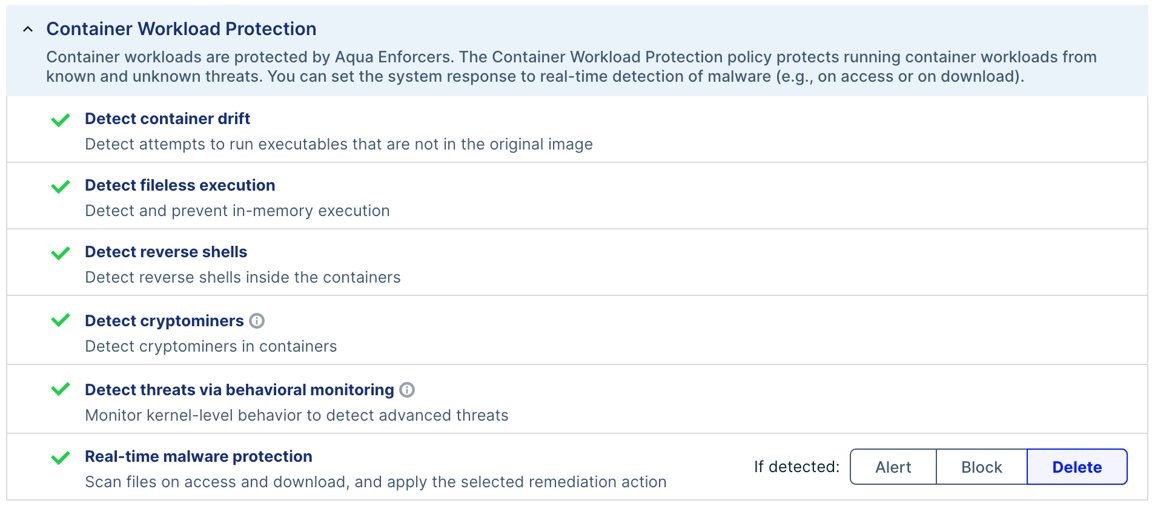
eBPF technology makes deployments safe and provides kernel level visibility. Behavioral indicators from Aqua Nautilus pick out advanced attacks based on observations of real cloud native attacks in the wild. This gives you the information you need to contain and mitigate an attack in realtime, identifying sophisticated attacks like fileless malware and rootkits.
Protect your workloads
Use these questions to evaluate runtime solutions:
- Ask whether a product can see fileless malware attacks or a process executing from memory.
- Ask whether a product can stop an attack in production without stopping the workload.
- What mechanisms are in place to stop attack escalation or lateral movement?
- What are the estimations of your MTTD and MTTR?
- Which type of coverage do you have during Dwell Time, or even before it?
- Do you have an out-of-the-box runtime capability that can stop advanced attacks?
Watch how Aqua’s Runtime protection solution can protect you against zero day attacks in realtime, with rapid deployment in this runtime security demo. Learn about the continuing importance of runtime security and how to build an effective runtime strategy in this webinar. Reach out to our sales team today to see the next generation of runtime first-hand in a live environment.

