Because of the intricacies of cloud native environments, threats are not only becoming more frequent, but the tactics used rapidly change. Thus, making the need for security professionals to understand these ever-changing tactics more important. Aqua Nautilus, our team of cybersecurity researchers, has analyzed attacks that were observed in the wild over the past year to highlight the latest developments in the threat landscape. The result of this research and analysis has been compiled into the Aqua Nautilus 2023 Threat Report.
The report focuses on three key areas and the related threats: software supply chain, risk posture, which includes vulnerabilities and misconfigurations, and runtime protection. The report shines light on the ever-changing tactics and techniques.
Interdependency Makes Software Supply Chain Attacks Increasingly Appealing
Data from Aqua’s software supply chain team showed that software supply chain attacks grew by more than 300% year-over-year. It is easy to see why, because cloud-based software systems are highly interdependent and consist of multiple layers of components that interact with each other. It is the layers that prove challenging to secure, but it is interdependency that makes software supply chain attacks so appealing to attackers. They offer a gateway to sensitive data and a launch point for massive cyberattacks. Additionally, they offer the ability to move laterally in the cloud to other services and private cloud infrastructure.
The report looked at services such as GitHub, PyPI, Ruby, and NPM which are frequently targeted by threat actors as a way to deliver and execute malicious code. It also dives into attacks such as a new phishing-as-a-service against code and package managers and how it is used to bypass multifactor authentication mechanisms, leading to potential session cookie hijacks and account takeovers. It discusses how threat actors can exploit software packages and use them as attack vectors to subvert the software supply chain. It also explores the “shift-left-left,” phenomena in which attackers are now targeting the developers themselves.
Vulnerabilities Emerge Across SDLC and Misconfigurations Not Taken Seriously Enough
Robust and common practices in cloud security include finding and patching vulnerabilities and locating and fixing misconfigurations. These are key components in any software security management, let alone in the cloud.
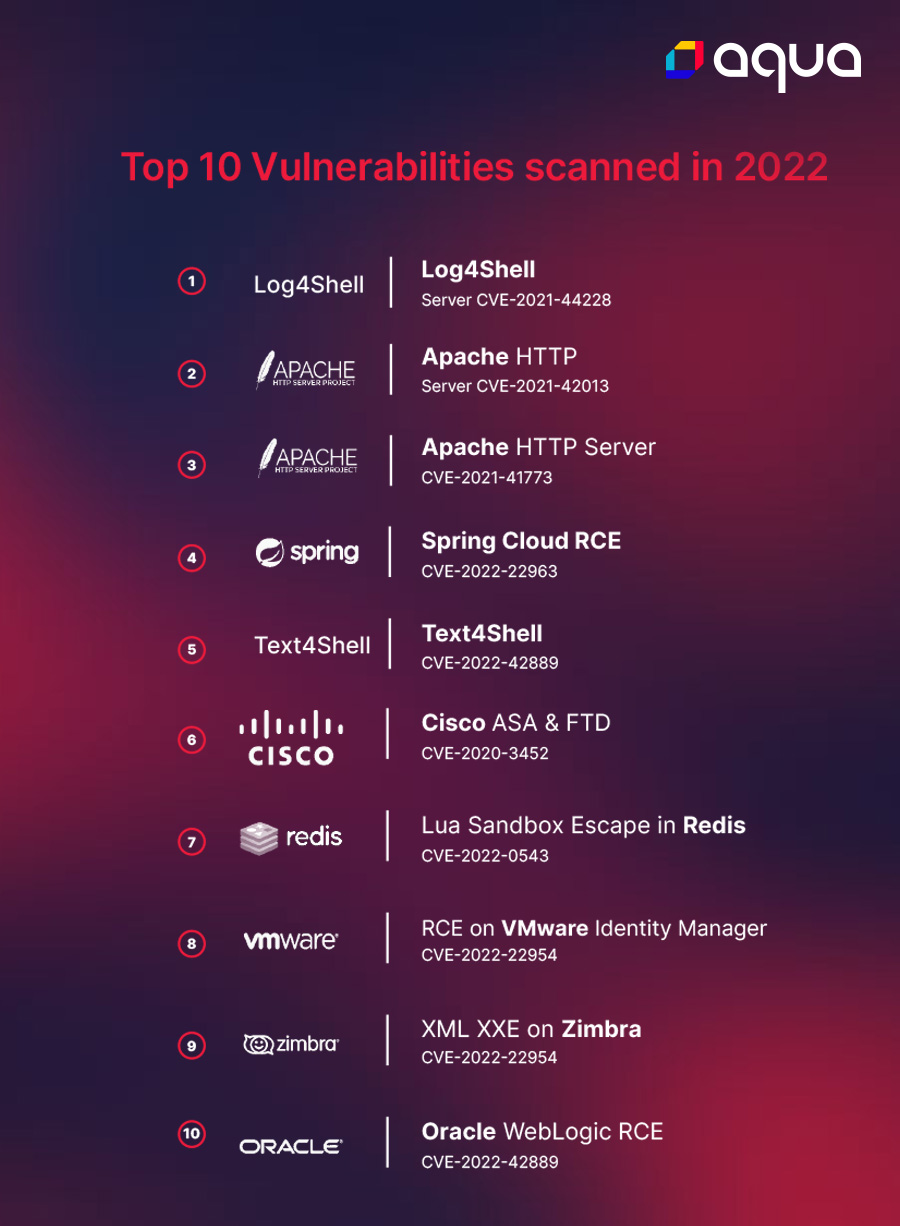
Vulnerabilities continue to emerge across virtually every stage of the cloud Software Development Life Cycle (SLDC), and hackers will continue to exploit the weakest areas that have the highest impact in the future. While Log4Shell may have gained the biggest headlines, the top 10 vulnerabilities scanned in 2022 were mostly related to the ability to conduct remote code execution (RCE). This reinforces the idea that attackers are looking for initial access and to run malicious code on remote systems. Additionally, we see that Apache servers and services are widely targeted as Log4Shell, Text4Shell, Spring Framework, and other services are all related to Apache.
The report also showcases the distribution of CVE by publication year as well as the distribution of the CVSS V3 score.
Misconfigurations often arise due to human error, lack of knowledge or experience, or mismanagement of cloud resources. Simple mistakes could lead to catastrophic consequences, including data breaches, loss of sensitive data, and service disruptions.
The report looked at the criticality of misconfigurations and how they aren’t being taken seriously by organizations yet pose a real threat of attack. Aqua Nautilus researchers observed organizations of all sizes at risk for misconfigurations, finding one example where more than 25,000 distinct servers or smaller organizations were vulnerable because of misconfigured Docker Daemons. Each of these servers were exposed on average for 56 days, or almost two months — ample time for an attacker to find and exploit them.
Hackers Focus on New Ways to Avoid Detection
The complexity of businesses cloud environments presents a large attack surface for hackers. This includes various applications, that can lead to misconfigurations and vulnerabilities, which have made it almost too easy for a hacker to avoid detection. In fact, this year’s report has found that 50% of the attacks in this year’s report focused on defense evasion.
With so many threat actors using techniques to conceal their campaigns we compared this with Aqua Nautilus prior research in 2022 and found there was a 1,400% increase in fileless attacks. Indicating threat actors are focusing on more ways to avoid detection and establish a stronger foothold in the compromised system.
Runtime Security Remains a Critical Last Line of Defense.
Tactics continue to evolve either finding new targets that are skilled in their craft but often lack security knowledge and skills, finding valuable targets who have the power to access various applications and data environments within the organization or the most proliferated tactic evading agentless solutions.
Protecting runtime environments requires at least a monitoring approach that includes scanning for known malicious files and network communications, then blocking them and alerting when they appear. However, this is still insufficient. A better solution includes monitoring for indicators or markers that suggest malicious behavior as well – for instance, behaviors such as unauthorized attempts to access sensitive data, attempts to hide processes while elevating privileges, and the opening of backdoors to unknown IP addresses. It is critical to implement robust protection measures in runtime environments to ensure that data and applications are secure and to avoid being vulnerable to attacks.
The most persuasive evidence for the threat actors’ increasing and successful efforts to evade agentless solutions was found in early 2023. Aqua Nautilus researchers discovered HeadCrab, a state-of-the-art, stealthy, Redis-based malware that compromised more than 1,200 servers. The level of its sophistication emphasizes the need for agent-based scanning to detect attacks designed to evade volume-based scanning technologies.
Protecting workloads in runtime environments is crucial for ensuring the security and integrity of business data and applications. This is where code executes, and threat actors are increasingly targeting these environments to steal data or disrupt business operations. One might argue that organizations have already hardened their runtime environments and implemented shift-left security practices to address vulnerabilities and misconfigurations in the source code.
Learning from Others
The distributed nature of cloud native applications and their components can make it challenging to identify and mitigate potential risks and threats. It’s critical to learn from the cumulative experiences of not just your organization but others as well.
That’s where Aqua Nautilus can help.
The Aqua Nautilus 2023 Threat Report aims to help provide insight to how threat actors might exploit your cloud native environments and the technological core of your business, what to look for, and even anticipate. Download the full report here.

