Linguistic Lumberjack is a new critical severity vulnerability (CVE-2024-4323) that affects Fluent Bit versions 2.0.7 through 3.0.3. The vulnerability involves a memory corruption error, potentially leading to denial of service, information disclosure, or remote code execution.
Fluent Bit is a highly popular open-source data collector and processor designed for handling large volumes of log data from various sources. With over 3B downloads and 10M daily deployments, it is widely used by all major cloud providers.
This vulnerability was discovered by the Tenable research team who described in their blog, that the flaw is due to improper validation of input names in requests, which can be exploited to cause memory corruption. This can result in denial-of-service attacks or information exposure, with remote code execution being possible under certain conditions.
At the moment, there isn’t any record of actual exploitation of this vulnerability in the wild. Additionally, we would also like to note to our customers that Aqua does not utilize Fluent Bit, and our analysis shows no evidence of sub-dependencies using this package therefore Aqua is unaffected.
Nautilus’ investigation of the CVE-2024-4223 vulnerability
According to the released writeups and PoCs, in order to exploit this vulnerability, the built-in http server needs to be exposed to the internet. We sampled 20 versions from various popular open source tools on Docker Hub (such as Fluent, Bitnami, Grafana, Ranher etc.), in all of them the http server was configured to be Off by default. In order to test the PoCs and create a honeypot we actually had to change the configuration to On to expose the built-in http server to the internet.
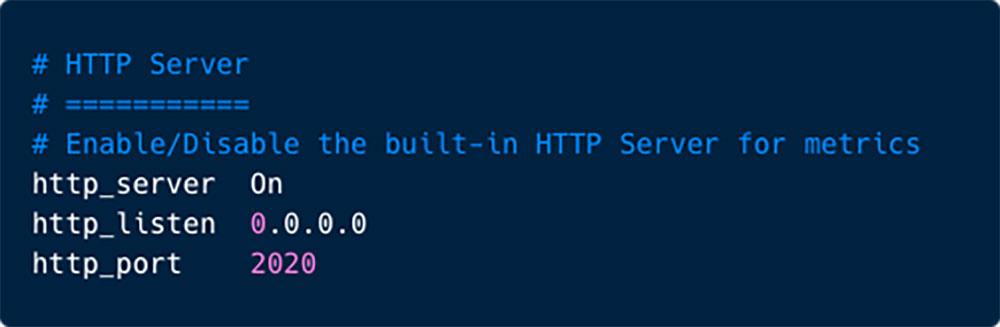
Figure 1: Changing the configuration to ‘On’ to expose the built-in http server to the internet.
We queried Shodan to further understand the scope of exposure of fluent-bit http servers, but our search didn’t yield any significant results on (fluentbit, fluent, and ports 2020 and 24224). We found 78 internet connected fluent-bit servers. Out of which only 24 (30%) had a vulnerable version between 2.0.7 and 3.0.3.
Detection and remediation with Aqua’s CNAPP
Utilizing Aqua’s cloud native application protection platform (CNAPP) you can both detect this vulnerability and prioritize it across your running workloads.
How can Aqua customers scan and detect the Fluent-bit CVE?
This security vulnerability (CVE-2024-4323) has been identified in the Fluent Bit open-source package and will be reported as such. Vendor packages for Fluent Bit will be shown as unaffected until the vendors publish an advisory for it. This information for the package or vendor packages can be accessed and/or downloaded on the Fluent Bit site.
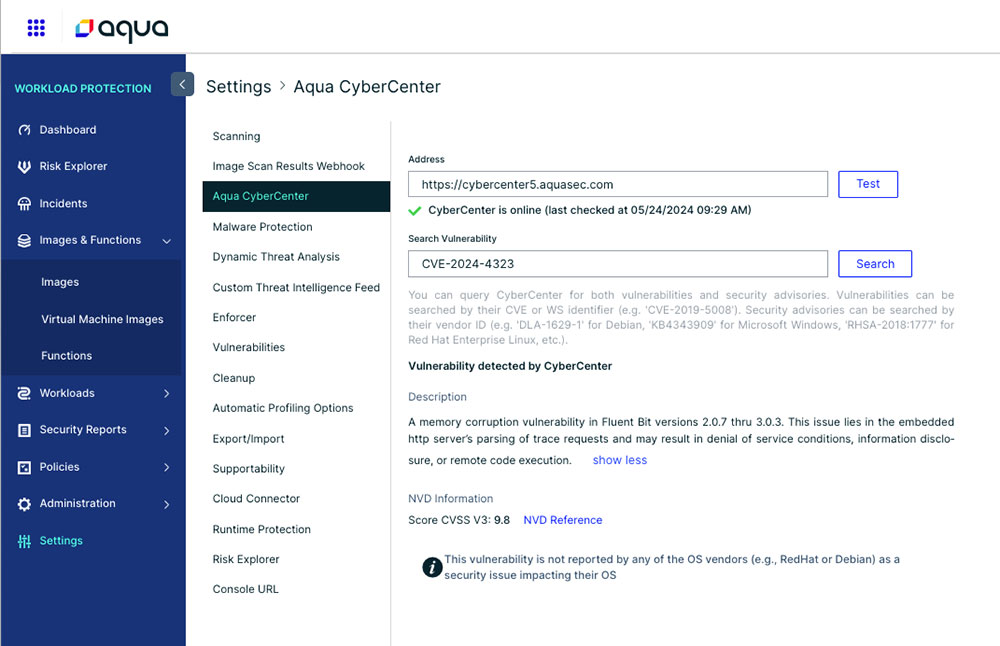
Figure 2: Aqua identifying the vulnerable fluent bit packages
Customers can scan their existing images with Aqua to gain visibility into their use of fluent-bit package. Aqua will identify the vulnerable fluent bit packages and report the CVE-2024-4323 on it.
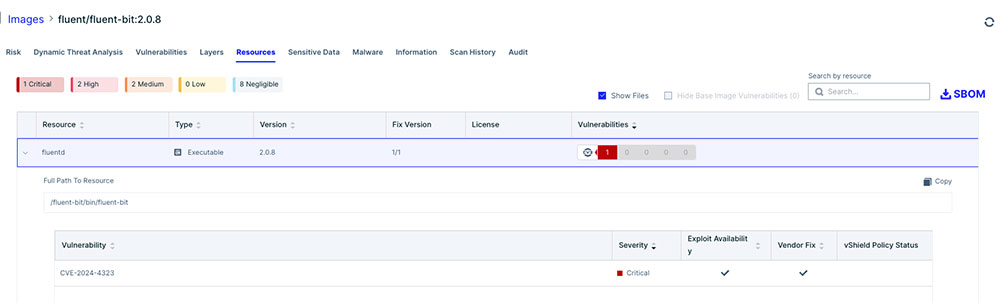
Figure 3 Aqua will present the information in the platform
The screenshot above shows how Aqua will present the information in the platform. So, while there are no indications of the CVE being exploited in the wild, there are, however, several Proof-of-Concept exploits released to GitHub, most of them are based on the one released by Tenable (d0rb, yuansec and skilfoy)that show how an attacker can cause denial of service conditions, information disclosure, or remote code execution by sending specially crafted trace requests. Thus, we are reporting this CVE as exploitable.
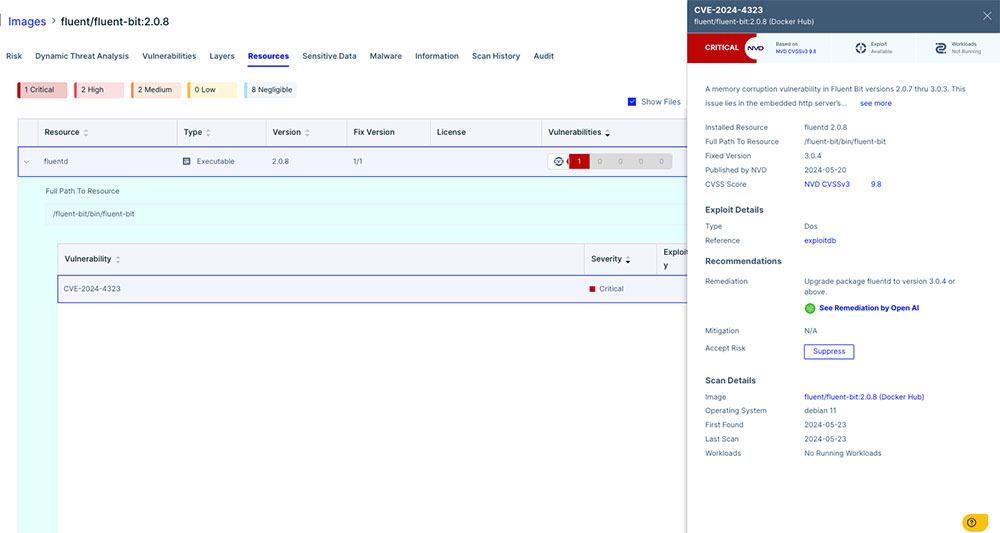
Figure 4: Reporting this CVE as exploitable
This proof-of-concept script demonstrates how a denial of service is used CVE-2024-4323 is a memory corruption vulnerability in Fluent Bit versions 2.0.7 through 3.0.3. It further shows how the issue resides in the embedded HTTP server’s parsing of trace requests, which can lead to denial of service (DoS) conditions, information disclosure, or remote code execution (RCE), enabling remote code execution.
For a full review of how Aqua can help watch our video below.
Immediate actions you can take now
The primary and most effective measure is to upgrade Fluent Bit to the fixed version 3.0.4. Users are advised to update to version 3.0.4 immediately. More information about the fix can be found here: v3.0.4
Additionally, we recommend limiting access by restricting access to the vulnerable HTTP endpoint as an additional precaution.
At Aqua Security, we remain dedicated to protecting our customers from cybersecurity threats through continuous vigilance and advanced security solutions. Our proactive measures ensure that they are safeguarded against vulnerabilities like CVE-2024-4323.

