When it comes to containerized workloads, resolving the underlying image’s security vulnerabilities is paramount to ensuring the safety of your environment. Getting security risk information into the hands of developers quickly and efficiently is key to keeping development cycles as short as possible while maintaining a strong application security posture. What risk information can you leverage and how do you share it across the development, engineering, DevOps, and Security teams? It all depends on the approach and toolkit you are using.
Finding and fixing image vulnerabilities at build
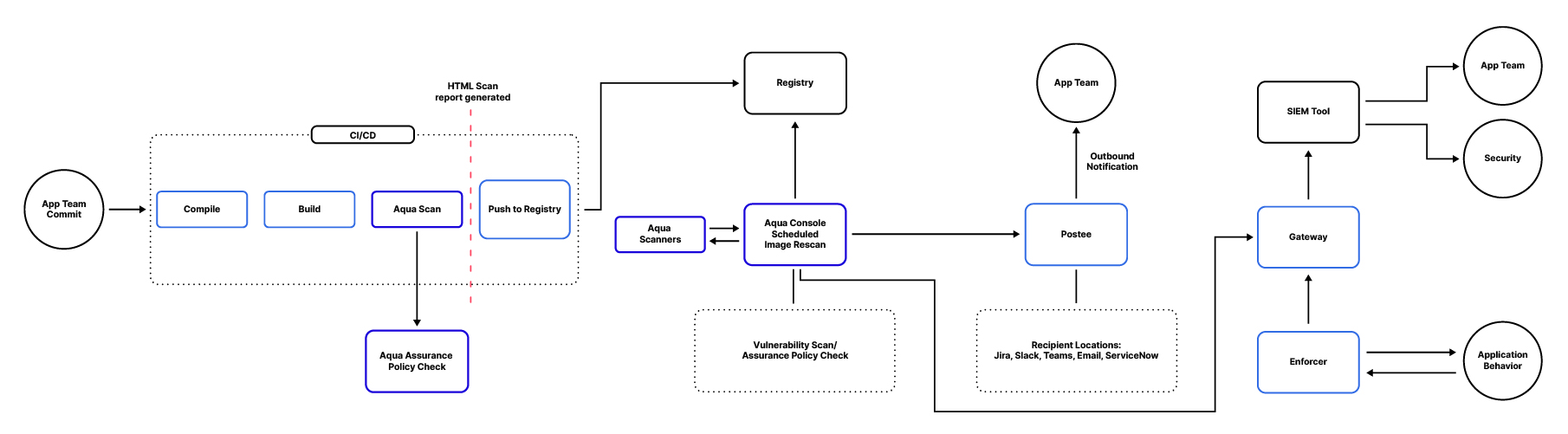
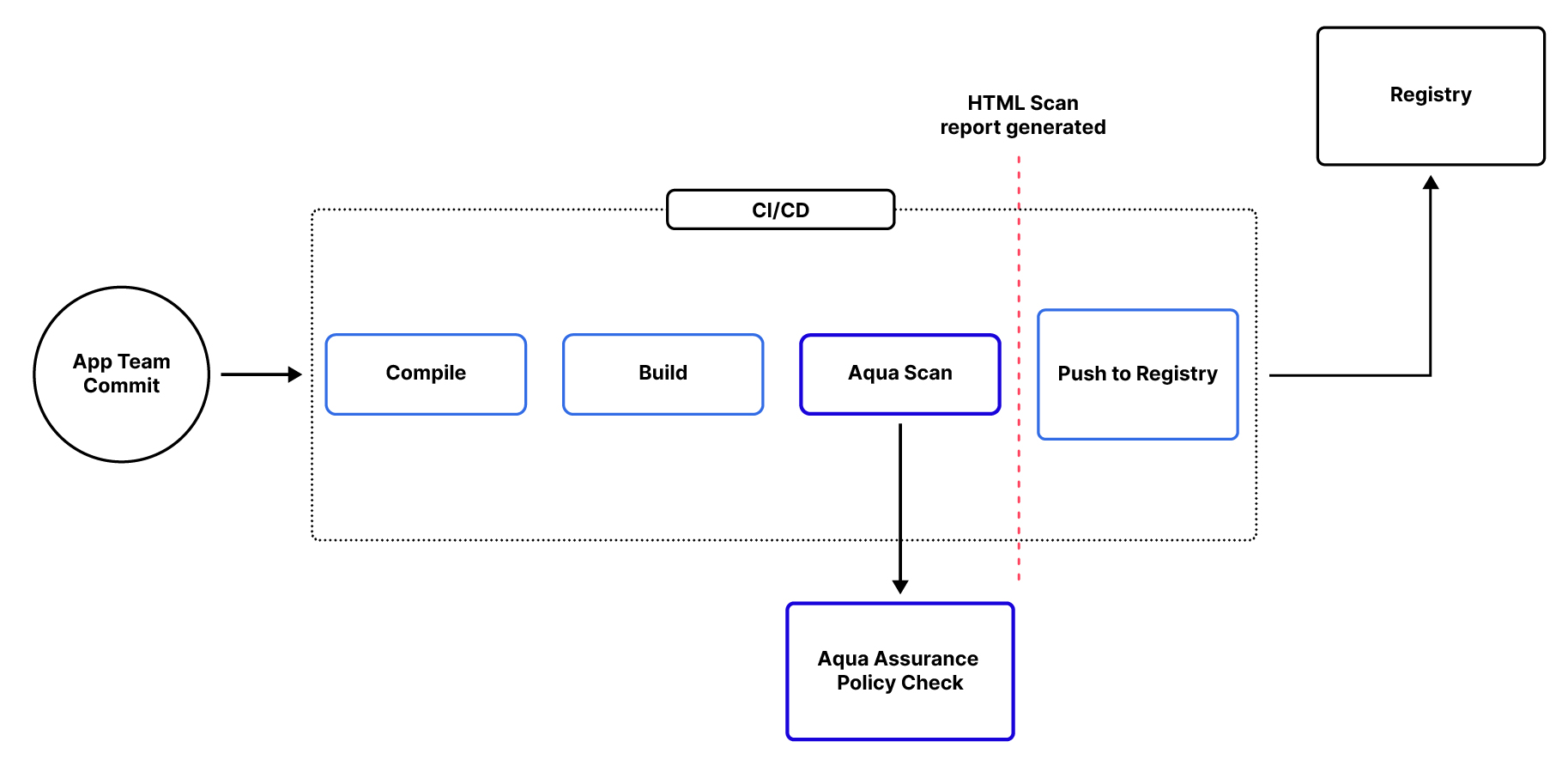
Adopting a shift-left mindset, you should scan your applications and identify risks as early in the development process as possible. In this blog, we’re introducing the Aqua Scanner into the build pipeline, which can be done via Docker command, plugin, or other means. The Aqua Scanner analyzes the desired image when a build is initiated, automatically providing security risk information directly into the hands of developers for rapid remediation before the process continues.
Security teams can ensure they manage the application’s security risk posture by establishing Aqua Assurance Policies against which the scan results are evaluated. This can automate critical alerts or trigger configured actions if the policy is violated. Additional insight is shared in the form of JSON, HTML, or Text output.
This provides multiple formats for developers or automation to take over and consume the reports, making any necessary changes to the application as a result. This feedback loop of analysis, insight, and action helps the pipeline to mature so images which proceed through it more consistently adhere to the policies. Stricter enforcement can be configured such that non-compliance with Assurance Policies can block a build, preventing those non-compliant images from being pushed to the registry.
The end goal for full CI integration would be to fail the pipeline for images that do not pass the Image Assurance policies and to allow it to proceed for images that pass. When the scan completes successfully, the –register-compliant argument can be used to cause the Aqua platform to save the results allowing the image to be executed. Other scanner options exist but do not allow for the assurance policy to influence the scan outcome.
Finding and fixing image vulnerabilities post build
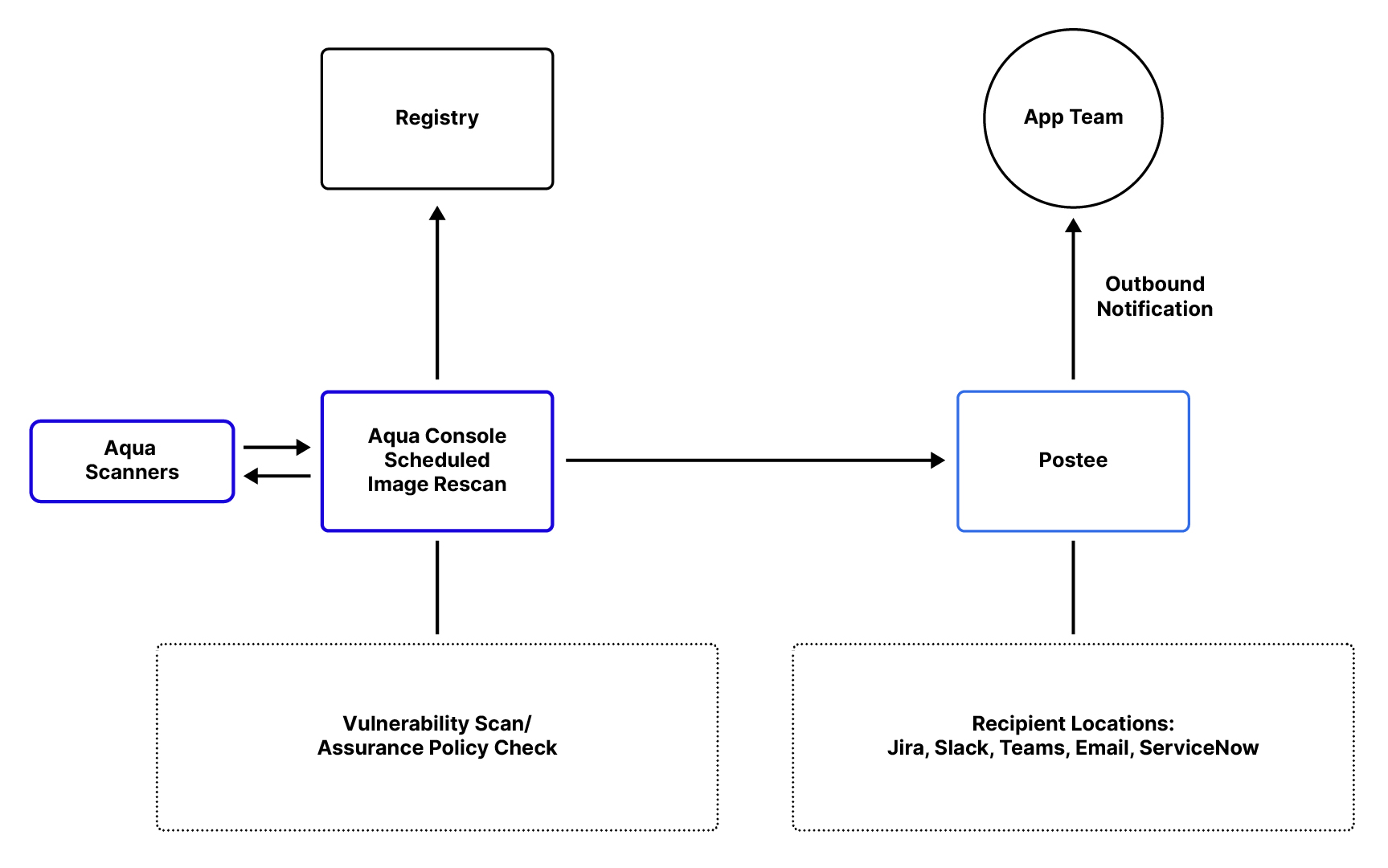
The containerized application lifecycle does not end, necessarily, with the CI/CD pipeline. Now that the image is available in the registry, it can be deployed on a given node and run as a container. Though that container is running, the underlying packages and resources are still susceptible to new CVEs as they are identified and potentially exploited. Due to this fact, Aqua rescans those registered images on a configurable basis to provide the most up-to-date security information on the registered applications.
Returning this information to stakeholders in Development, Security, and Operations is vital, since these applications may still be live and running in the environment. To facilitate such a workflow, Aqua has implemented a reporting tool called Postee.
As the scans are completed on the configured interval, Postee updates with the results and – based on your predefined configuration – sends them to the respective team and/or platform for prioritization and remediation. Commonly, this is coupled with Aqua’s RBAC functionality, where application scopes have the capability of including an owner’s email address for immediate notification. Postee is capable of utilizing this value as a dynamic recipient and sends emails accordingly.
Analyzing the running application’s behavior
Just as the underlying container image is now secure and being monitored for new vulnerabilities, the same must be done as the application is running. This may include identifying deviations from normal container activity or based on compliance status with runtime policies. This information is relayed by the Aqua Enforcer through the Gateway and, ultimately, to the configured SIEM tool of choice. There, your SOC team (or equivalent) can monitor for potential policy violations and either forward those results to the corresponding teams or to Security for further analysis, prioritization, and action.
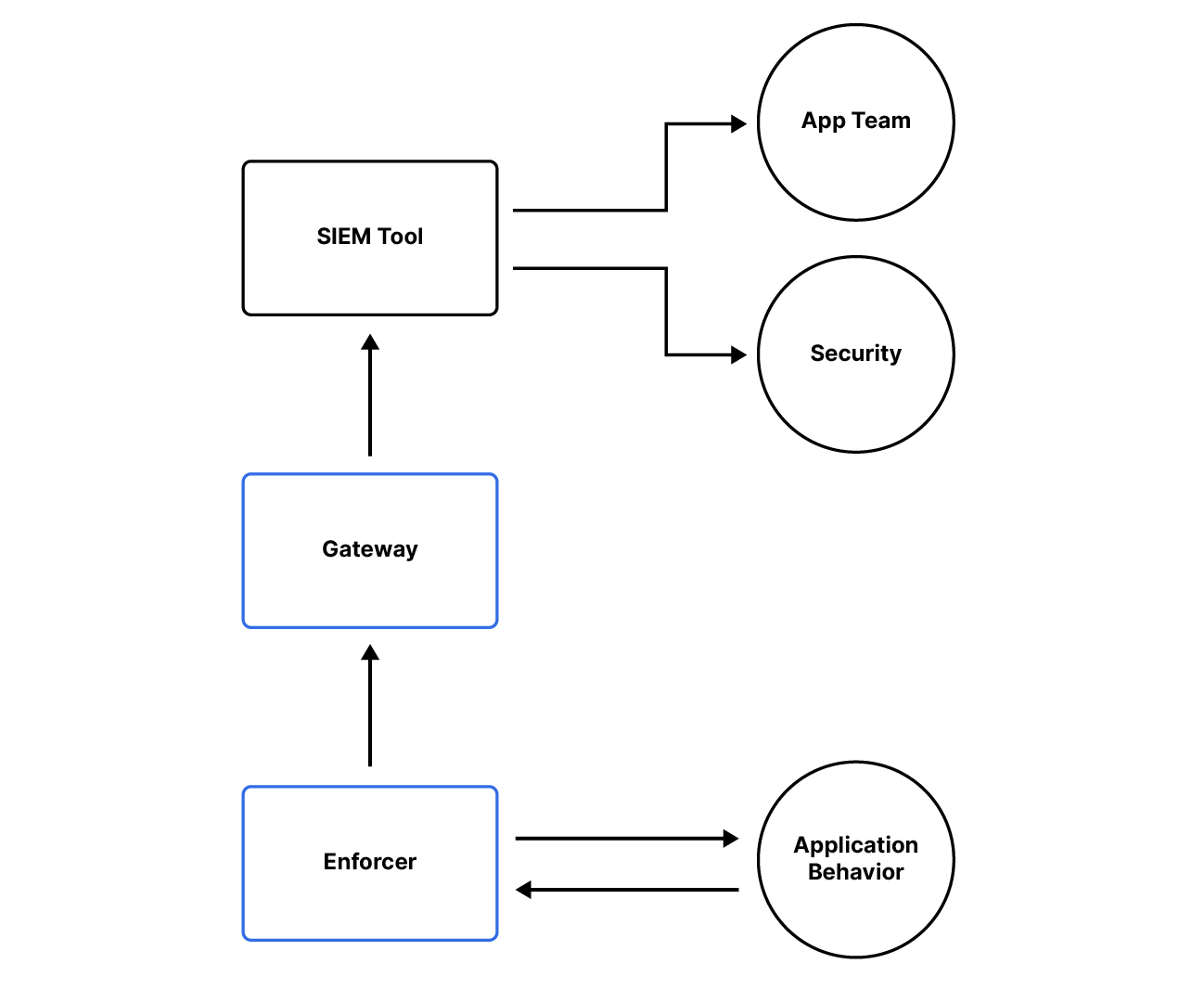
Conclusion
Security does not end with the initial evaluation of the image but extends well into the lifecycle of the artifact itself and its continuous delivery into the environment. This requires consistent monitoring and alerting to ensure these security gaps are identified and addressed quickly. Integrating the Aqua Scanner into the CI pipeline, configuring Postee to handle daily scan result notifications, and leveraging SIEM tools for runtime events can greatly improve your security posture and limit exposure or exploitation.