Today, OpenSSL announced two new CVEs and mitigation recommendations. This blog provides guidance as to how you can identify the Open SSL vulnerability using Trivy. To both identify and mitigate the vulnerability, see this blog post Updated Security Advisory: New OpenSSL Vulnerabilities about mitigation with assurance policies in Aqua’s software supply chain solution.
Package installed via OS package manager
If you have the OpenSSL package installed through your operating system package manager (e.g apt-get, yum, apk, etc), Trivy will detect it.
The following screenshot shows Trivy scanning the nginx container image which has some important OpenSSL related vulnerabilities. The latest OpenSSL vulnerability will be detected and displayed similarly. Note that to show only OpenSSL related vulnerabilities, we have used an optional Trivy filter that is dedicated for this search.
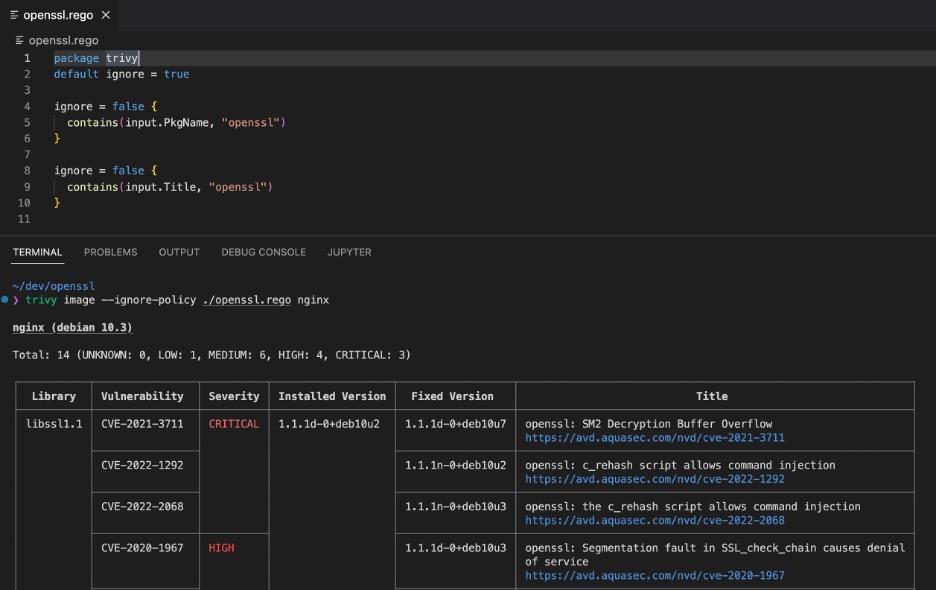
Now you have found the vulnerable package. But you will also need to find the package that needs to be upgraded.
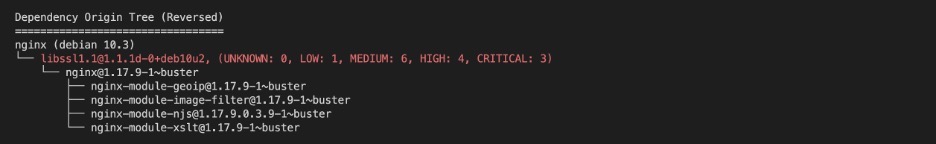
The following shows the result of the same Trivy scan, this time with the –dependency-tree flag that detects the vulnerability and traces it to its origin packages. Trivy can reproduce the reverse dependency tree of the vulnerable package, essentially showing you the actual package that should be upgraded. Finding the vulnerable package is not enough because often it will be a dependency of another application you’ve installed. For example, nginx package might depend on openssl, and, in order to fix the issue, you would need to upgrade nginx and not openssl directly.
Package installed via Conan package manager
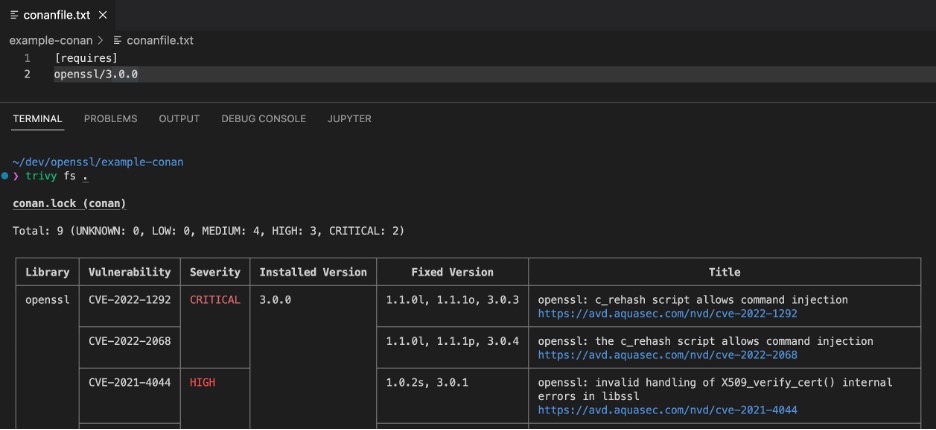
If your application uses the Conan package manager for CC++, Trivy can find the installed package through the Conan lockfile.
The following shows Trivy scanning a code repository with OpenSSL 3.0.0 which has some important vulnerabilities. The new OpenSSL vulnerability will be detected and displayed similarly.
Unpackaged binary
Some containers include applications that were installed without a package manager such as a Dockerfile that builds and copies the binary to the resulting container image.
When scanning such artifacts, any security scanner will have difficulty identifying the application and its dependencies. But Trivy has an innovative feature that can help. It is becoming increasingly common for developers to manage and declare their application’s dependencies proactively in a software bill of materials (SBOM) and store it in a common directory, such as Sigstore. In this case, Trivy will be able to identify the executable binary during the scan and discover its matching SBOM in Sigstore automatically! Learn more in the blog Trivy Can Now Scan Unpackaged Binary Files.
Scanning containers in Kubernetes
Trivy can be installed in Kubernetes using the Trivy Operator. Trivy Operator automatically scans all of your workloads and creates Kubernetes-native Custom Resources for informing you of vulnerability reports.
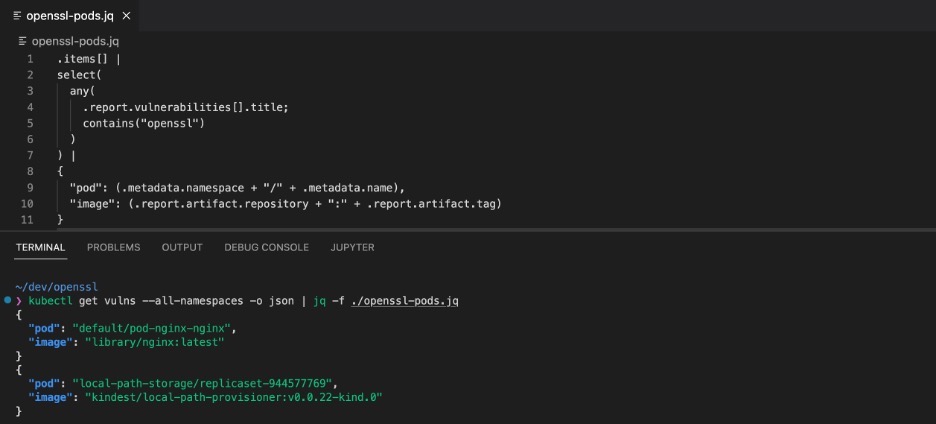
The following shows how you can check for OpenSSL related vulnerabilities across all workloads in cluster by examining the generated Vulnerability Reports. Note that the jq utility is used to filter only OpenSSL instances and to construct a report that includes only affected workloads:
Conclusion
Trivy is a quick way to immediately get a view into your exposure for the OpenSSL vulnerability. Visit the github page to get started today.

