Many of our customers run container workloads on AWS – hardly surprising given Amazon’s lead position in the cloud market. But AWS also offers some distinct advantages to those running containers, including a set of highly-integrated services that take the pain away from managing deployments.
Aqua has supported container deployments on AWS pretty much since the beginning, but until now we haven’t shared exactly how this is done and the benefits it provides. I’m here to rectify that.
Amazon EC2 Container Service (ECS) is a highly scalable, high performance container management service that supports Docker containers and allows you to easily run applications on a managed cluster of Amazon EC2 instances. Amazon ECS eliminates the need to install, operate, and scale your own cluster management infrastructure. With simple API calls, you can launch and stop Docker-enabled applications, query the complete state of your cluster, and access many familiar features like security groups, Elastic Load Balancing, EBS volumes, and IAM roles. You can use Amazon ECS to schedule the placement of containers across your cluster based on your resource needs and availability requirements. You can also integrate your own scheduler or third-party schedulers to meet business or application specific requirements.
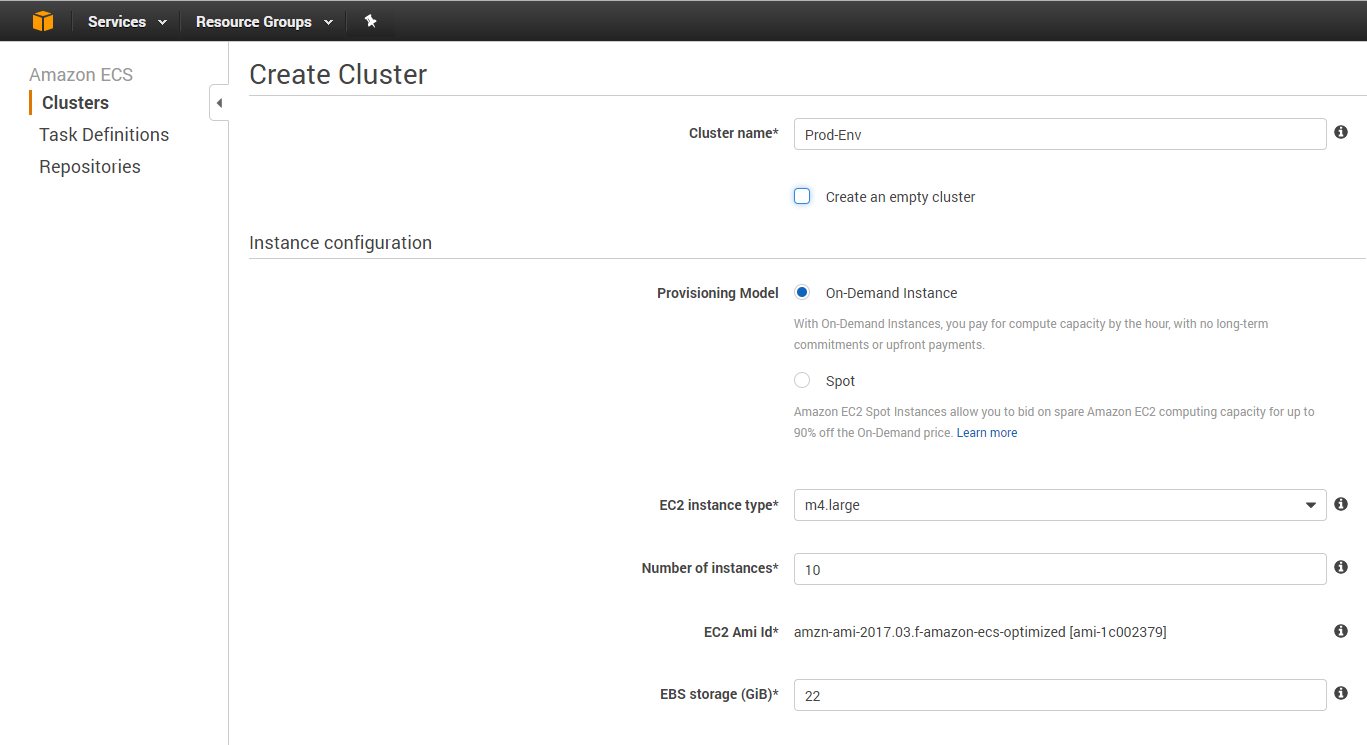
An Amazon ECS cluster is a logical grouping of container instances that you can place tasks on.
It only takes two steps to create a cluster:
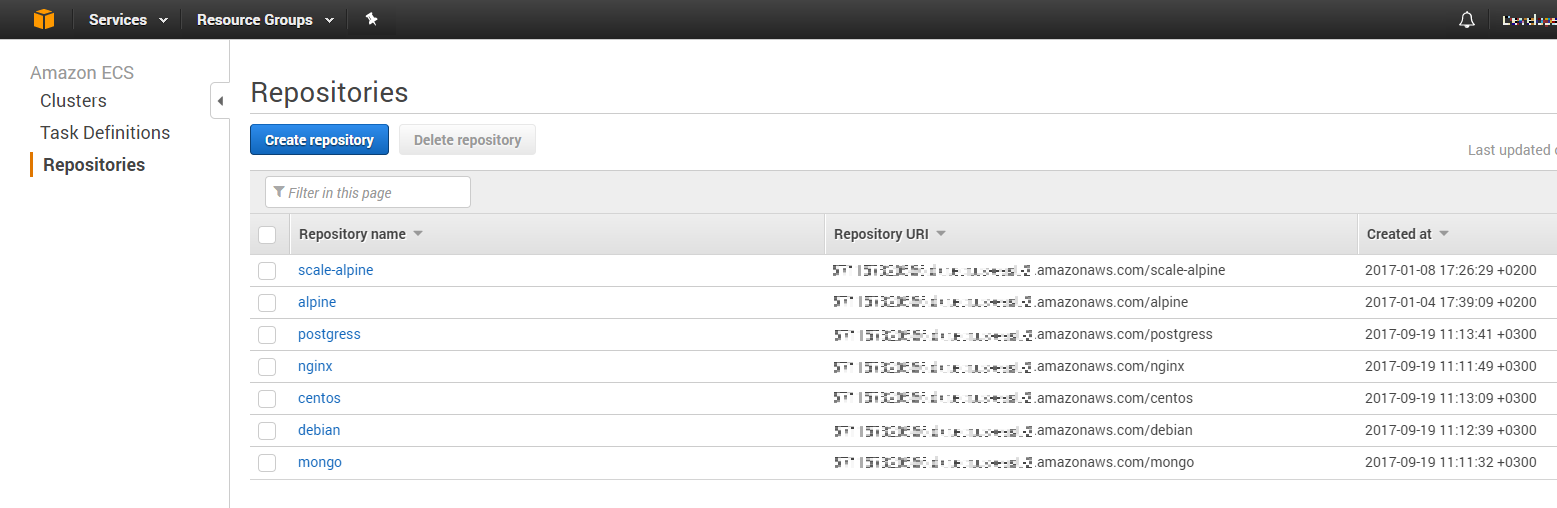
Amazon EC2 Container Registry (ECR) is a fully-managed Docker image registry that makes it easy for developers to store, manage, and deploy container images. Amazon ECR eliminates the need to operate your own container repositories or worry about scaling the underlying infrastructure.
Using Aqua to Secure Container Workloads on AWS
Aqua security integrates seamlessly with these products by Amazon and provides important security capabilities on top of Amazon’s management capabilities.
Aqua on AWS Deployment Topology
Deploying Aqua on Amazon AWS
Aqua product is a container security platform that is itself delivered in container form (yes, we eat our own dog food…!)
It is super-easy to deploy Aqua on ECS environments – simple deploy a set of ECS deployment descriptions that will run the following Aqua components:
- Aqua Enforcer
Deployed as a container on each and every ECS node. The Enforcer provides visibility into the activity of containers running on the same node, as well as control over certain activities that enables Aqua to prevent suspicious or malicious actions from taking place.
- Aqua Command Center
Management console used for defining security policies and viewing container activity. It is also used for vulnerability scanning of Amazon ECR. - Aqua Gateways
Provide connectivity between Aqua Command Center and the Enforcers. You can scale-out deployment between Enforcers in different availability zones by adding Aqua Gateways in every zone.
Continuous monitoring of Amazon ECR
Most DevOps and security professionals would agree that it is both important as well as easier to secure containers early their lifecycle. Aqua “shifts left” the security controls and applies them as part of the CI/CD pipeline – but it is as important to have continuous monitoring of all images to make sure that the production environment is kept secured as time goes by.
You can achieve this by integrating Aqua with Amazon ECR. After a quick one-step configuration you can automatically scan ECR images for vulnerabilities, check their security status and apply image assurance policies that will ensure that only approved images are allowed to run.
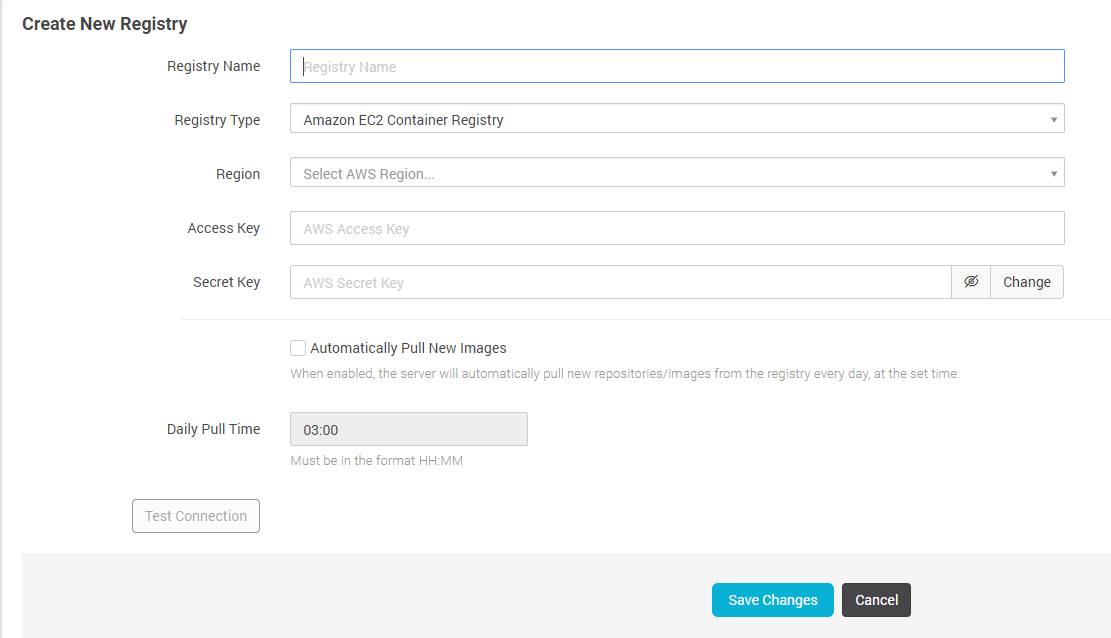
Easily integrate with your ECS Container Registry
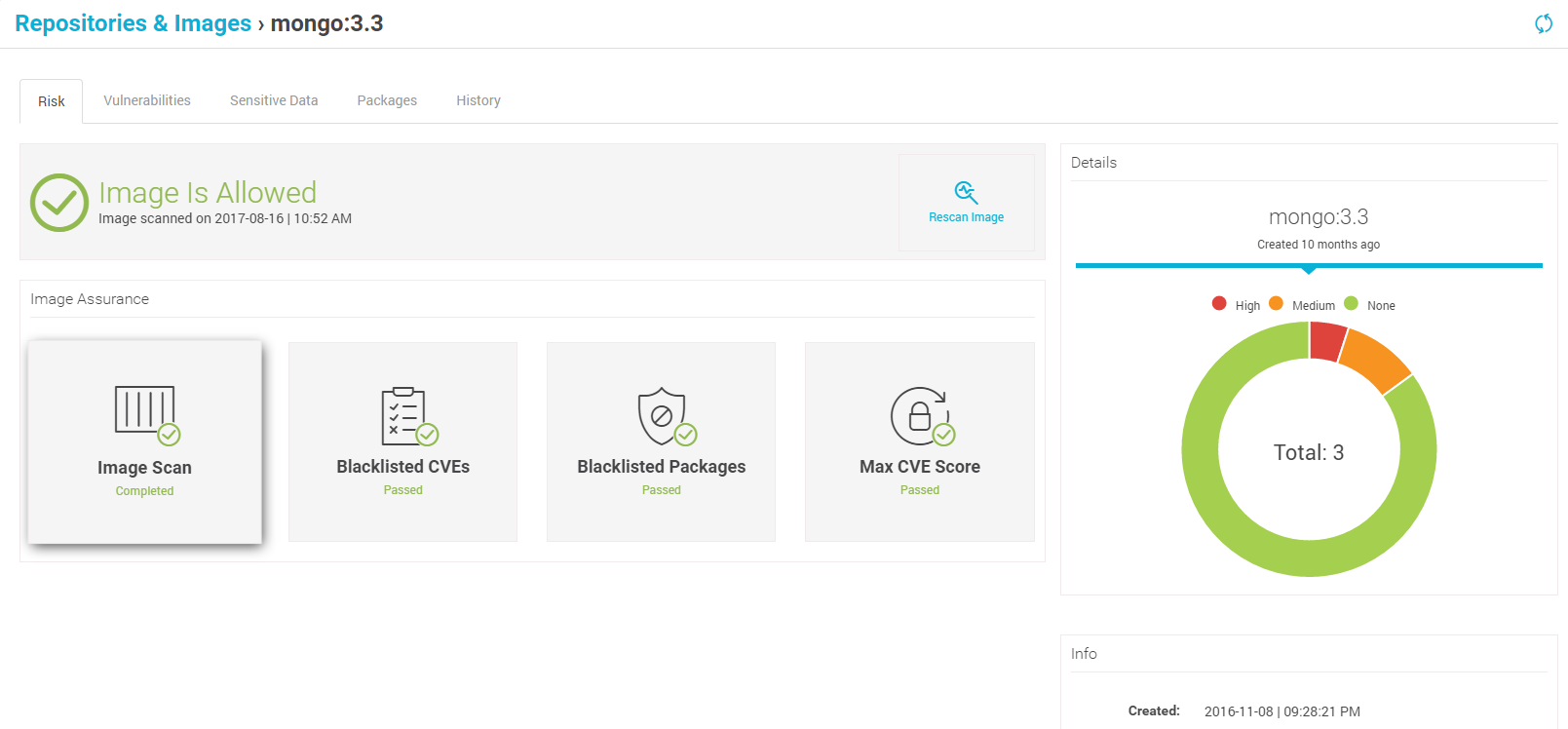
Approve images based on risk assessment
Runtime Protection for Amazon ECS
During runtime, and especially when containers are deployed in production environments, having vulnerability-free images is a good starting point, but is insufficient to stop attacks, user privilege abuse and malicious or compromised container activity. This is done by the Aqua Enforcers.
The deployment of Aqua Enforcers is such that Amazon ECS manages them, meaning that every new node to come up as part of the relevant services will be covered by Aqua automatically.
Deploying Aqua Enforcer on every ECS node allows you to apply machine-learned runtime controls on your running containers. These Runtime profiles whitelist normal behavior, and make it easy to detect anomalies and escalation attempts. They capture and enforce container activity such as: which read-only files can be accessed by the container, inbound and outbound network connections, allowed executables, whether the container can run as root, what storage volumes are allowed, as well as resource limits on simultaneous processes, CPU and memory usage.
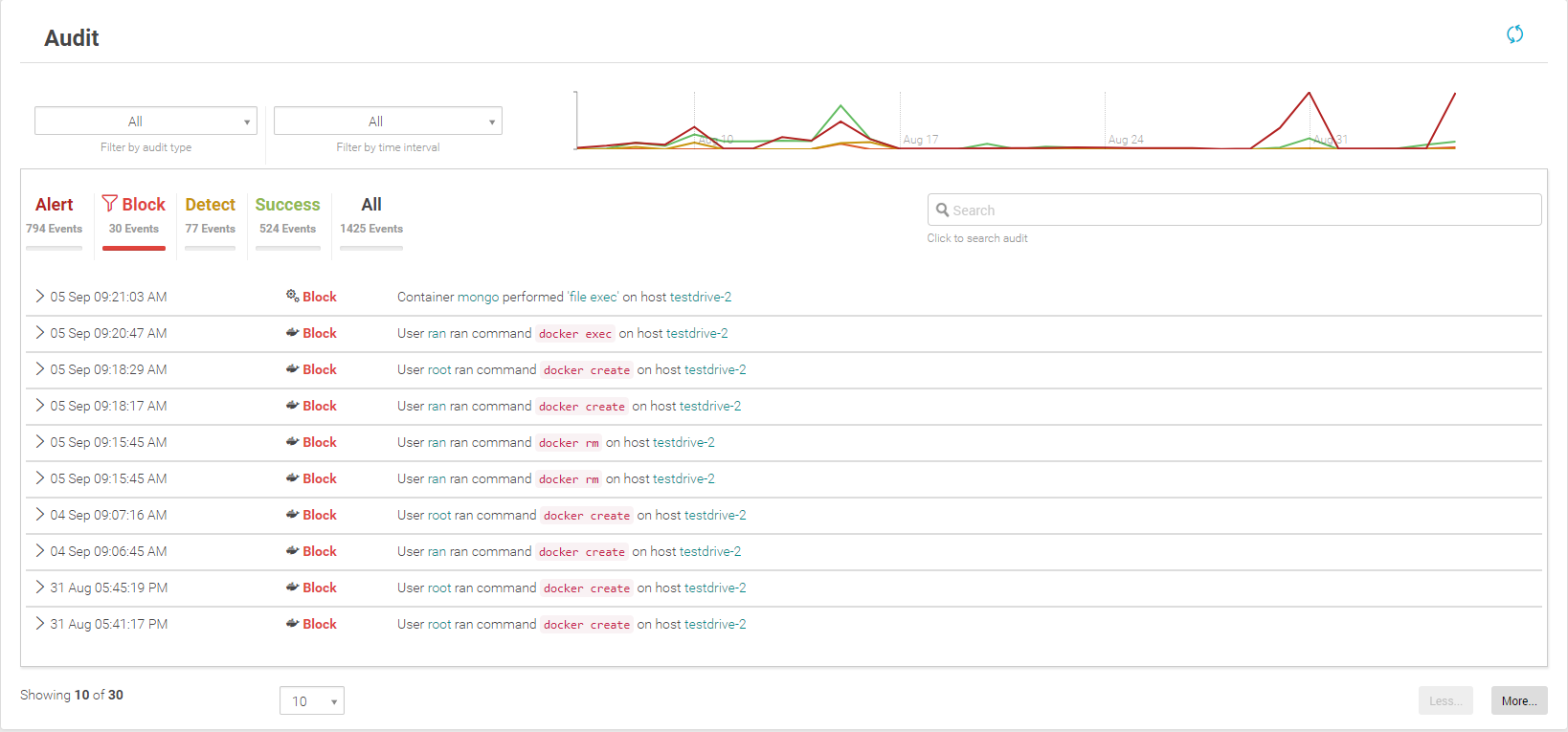
Get visibility into container events in runtime and block suspicious activities
Container Secrets Injection with Amazon KMS Integration
On top of the continuous image assurance and runtime protection, Aqua integrates with another AWS product – Amazon Key Management Service (KMS).
AWS KMS is a managed service that makes it easy for you to create and control the encryption keys used to encrypt your data, and uses Hardware Security Modules (HSMs) to protect the security of your keys.
With Aqua you can encrypt secrets stored in AWS KMS and distribute their values securely through Aqua’s access control system to running containers. All you need to do is to configure the AWS KMS details in Aqua server and you can immediately manage container’s access to KMS secrets from Aqua UI. If you need to change or rotate secrets, you do that in AWS KMS, and the secrets will automatically be updated in the relevant containers, with no need to restart the containers.
The secrets are never stored on disk, and are not visible on to anyone or anything but the intended container. In this way, Aqua secures the “last mile” of the secrets’ journey.
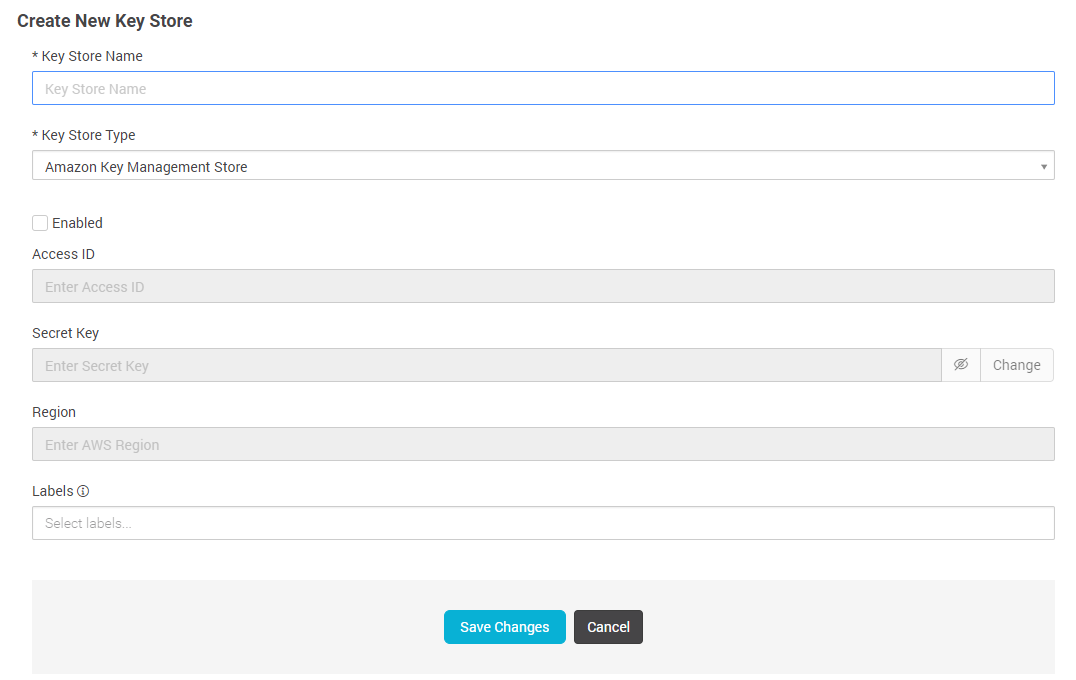
Integrate AWS KMS for managing secrets in containers
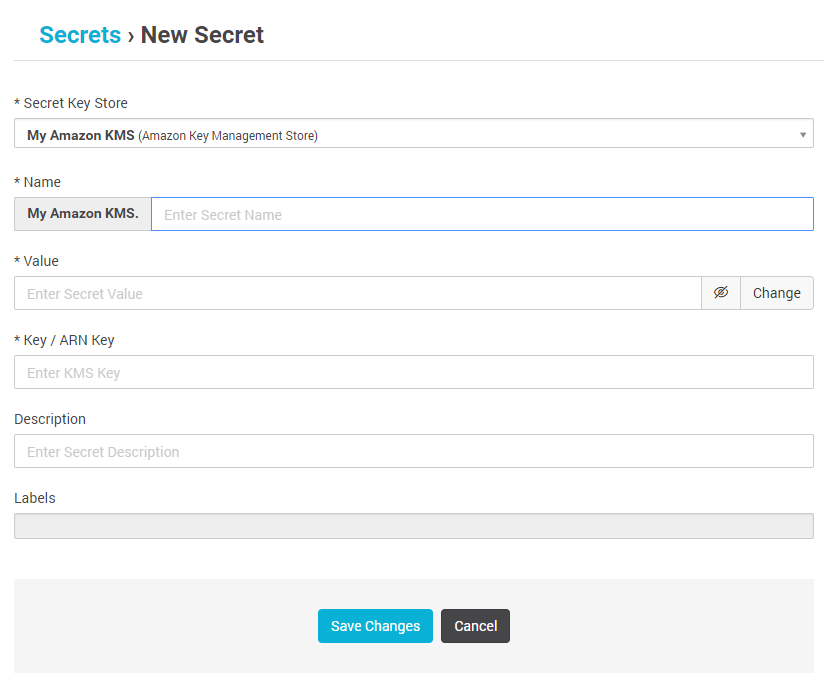
Assing secrets to containers by labels
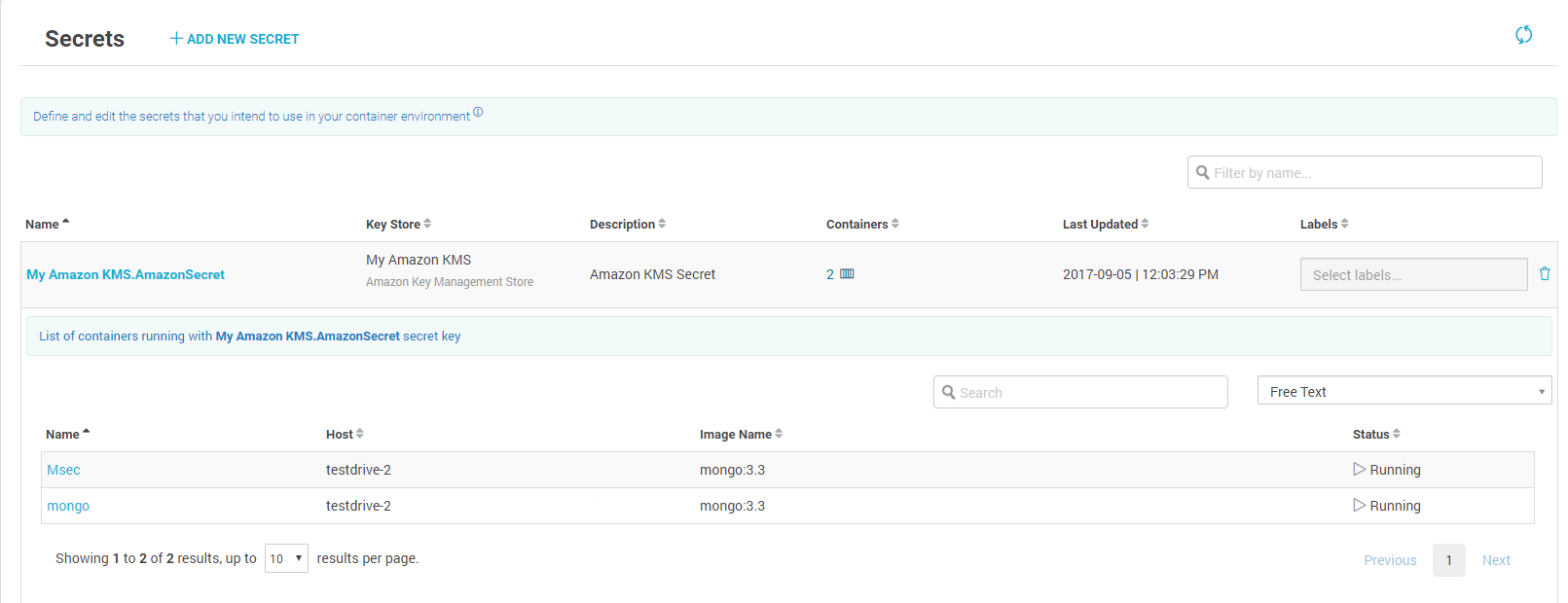
View which containers use which secrets – update, rotate and revoke secrets
In Summary…
AWS has a full stack of great services for managing your container environment. Aqua’s seamless integration with mutliple AWS tools makes it easy to to secure the entire container DevOps chain, as well manage secrets, and monitor and protect container workloads in runtime.
Read more on managing and securing Kubernetes secrets

